Using a termite colony as an example, we discuss the power of collective action when activating behavior change at scale.
Did you know that in Kenya, termites build mounds that reach 30 feet high and 80 feet across (9 x 24 meters)? According to this New York Times Science article, not only do the mounds have a sophisticated ventilation system that keeps them "cooler in the heat of the day and warmer at night", but "the mounds also protect their builders — against the sun that would desiccate them, the seasonal rain that would drown them, and the many predators that would happily devour them."
What's fascinating is that each termite carries out a comparatively simple set of actions. On the individual level, they don't achieve much. But, on the scale of thousands of termites, the collective impact is massive. They can change the structure of the landscape in complex ways.

The Power of Collective Action
This idea of changing or creating structures through simple, collective action is profound. The resulting structures affect what is possible – what forces can impact the group and what future behaviors are promoted or constrained.
Although this is a powerful idea, it isn't applied often enough to activate change in organizations. As a result, it's a missed opportunity.
Case Study: Information Security
Of course, collective action is not limited to termite mounds. It has a powerful role to play in your everyday work and life. Let's consider information security (Infosec) as an example. Many of us use our social media accounts to sign in on websites, which is risky. Ideally, we should be logging in without third-party apps. The risk to using this method is that if hackers figure out your social media passwords, they essentially have access to your entire online presence.
Traditional Infosec programs focus primarily on knowledge transfer. The learner watches some videos, reads some text, or plays some games, and afterward, they answer some questions to see if they retained any information. Meanwhile, back at work, they become busy, tired, or distracted and neglect to apply the security practices they learned. The vulnerability remains.
Cognician has a different approach. Instead of the program inviting a user to spend time on a video, article, or game, the program simply nudges the user to spend the same amount of time on an action:
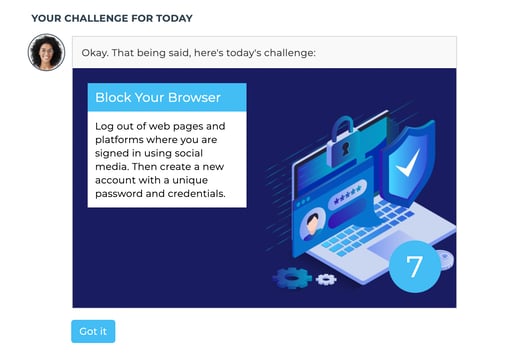
Every day, a learner will complete a range of challenges that take a few minutes for a set number of days. This challenge doesn't demand much time, skill, or motivation, so many people will collectively follow through on this simple action.
These sustained actions will change virtual structures on the web, leading to an immediate boost in security for the organization. Like the termites, this protects the organization from the criminal equivalent of the sun, rain, and predators that would harm them.
How can you apply this powerful idea in your organization? Sign up for a free trial today.


.png)

